Welcome to Us
CyberSecurity


How secure are you today?
Identify security objectives
Assess current security state
Provide customized recommendations and best practices
Create an actionable security roadmap

Cloud security is a shared responsibility

Every system, architecture, and application needs to be designed with security in mind. There’s too much at risk. For instance, a denial of service attack could prevent your customer from reaching your web site or services and block you from doing business. Defacement of your website damages your reputation, and a data breach could be even worse — as it can ruin hard-earned trust, while causing significant personal and financial harm. As a CSP we work hard to guarantee the security of our customer systems.
Organizations face many challenges with securing their datacenters, including recruiting and keeping security experts, using many security tools, and keeping pace with the volume and complexity of threats.
As computing environments move from customer-controlled datacenters to the cloud, the responsibility of security also shifts. Security of the operational environment is now a concern shared by both cloud providers and customers. By shifting these responsibilities to a cloud service like Azure, organizations can reduce focus on activities that aren’t core business competencies. Depending on the specific technology choices, some security protections will be built into the particular service, while addressing others will remain the customer’s responsibility. To ensure that the proper security controls are provided, a careful evaluation of the services and technology choices becomes necessary.
Our Layered approach to security
Defense in depth is a strategy that employs a series of mechanisms to slow the advance of an attack aimed at acquiring unauthorized access to information. Each layer provides protection so that if one layer is breached, a subsequent layer is already in place to prevent further exposure. Microsoft applies a layered approach to security, both in physical data centers and across Azure services. The objective of defense in depth is to protect and prevent information from being stolen by individuals who are not authorized to access it.
Defense in depth can be visualized as a set of concentric rings, with the data to be secured at the center. Each ring adds an additional layer of security around the data. This approach removes reliance on any single layer of protection and acts to slow down an attack and provide alert telemetry that can be acted upon, either automatically or manually. Let’s take a look at each of the layers.
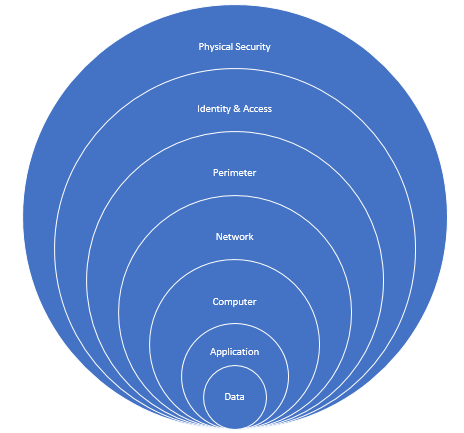
Our offering include
- Managed Security Services: Today’s rapidly evolving threat landscape demands smarter and more responsive managed security services. Techno World Managed Security Services offer the industry un-biased leading tools, technology and expertise to help secure your information assets around the clock, often at a fraction of the cost of in-house security resources.
- Infrastructure Security: Technoworld provides security to the infrastructure with broad set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing.
- Identity & Access Management: Technoworld enable organizations to define, develop, implement, and automate information access controls and privileges. IAM ensures only authorized individuals have access to the right data at the right time.
- Incident Management: Incident management is a common approach to create, support, and manage IT services, Technoworld respond to an unplanned event or service interruption to restore the service to its operational state.
- Application Security: Technoworld helps organizations to identify, fix and prevent security vulnerabilities in any kind of software application and almost every application has vulnerabilities. (to be discussed).
- Data Loss Prevention : Technoworld use a set of tools and processes to ensure that sensitive data is not lost, misused, or accessed by unauthorized users By classifying regulated, confidential and business critical data and identifying violations of policies defined by organizations or within a predefined policy pack, typically driven by regulatory compliance such as HIPAA, PCI-DSS, or GDPR.
- Network security: Technoworld provides protection to the usability and integrity of the network and data including hardware and software by targeting the threats to enter and spread in the network with effective and secure access to the network
- Cloud security: Cloud based systems, data and infrastructure protection through a set a policies and controls to ensure regulatory compliance and protection of customer data, by authenticating user access of applications, devices and networks.
- Internet of things (IoT) security: Technoworld secures the technology area concerned with safeguarding connected devices and networks in the internet of things (IoT) Allowing devices to connect to the internet securely.
Consulting Services
- Security GAP Analysis: Firewall Management, IPS/IDS, VPN, Access Control, IAM, End-Point Security, HBSS, Wireless Security
- Vulnerability Assessment: Technoworld provides a systematic review of security weaknesses in an information system by evaluating the system susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
- Penetration Testing: A penetration test is an authorised attempt to hack and gain access to an organisations data asset to identify vulnerabilities so that they are identified, and rectified before any potential cyber-attack, Technoworld penetration testing team demonstrates and conduct vulnerability and penetration tests and recommends remediation or mitigation
- Security & Compliance: Technoworld can help your organization protect the data you store in our cloud services and comply with legal and regulatory standards with variety of features and tools for data governance and protection.
- ISO ITSM 20000: The ISO 20000 is a Service Management System (SMS) standard, It specifies requirements for the service provider to plan, establish, implement, operate, monitor, review, maintain and improve an SMS. The requirements include the design, transition, delivery and improvement of services to fulfil service requirements.
- ISO ISMS 27001: SO/IEC 27001 specifies a management system that is intended to bring information security under management control and gives specific requirements. Organizations that meet the requirements may be certified by an accredited certification body following successful completion of an audit.
- PCI – DSS: The Payment Card Industry Data Security Standard is an information security standard for organizations that handle branded credit cards from the major card schemes. The PCI Standard is mandated by the card brands but administered by the Payment Card Industry Security Standards Council.
- GDPR: General Data Protection Regulation is a set of rules designed to give EU citizens more control over their personal data. It aims to simplify the regulatory environment for business so both citizens and businesses in the European Union to benefit from the digital economy.
- HIPPA: The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for sensitive patient data protection. Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA Compliance.
